This article gives a brief but detailed guide on the importance of cloud computing in e-commerce; and how its applications can help make your e-commerce business run smoothly, efficiently, and safely.
But first, let’s keep in mind what “cloud computing” is:
What is Cloud Computing?
Simply, it’s “on-demand availability of computer system resources,” but in reality, it goes beyond words. The term refers to the data centers that are not available on site but over the Internet comprising storage, analytics, networking, software, and intelligence. It works on a pay-as-you-go basis and lets you save and access your data anytime from anywhere.
Along with saving the cost, cloud computing applications lessen the data management complexity.
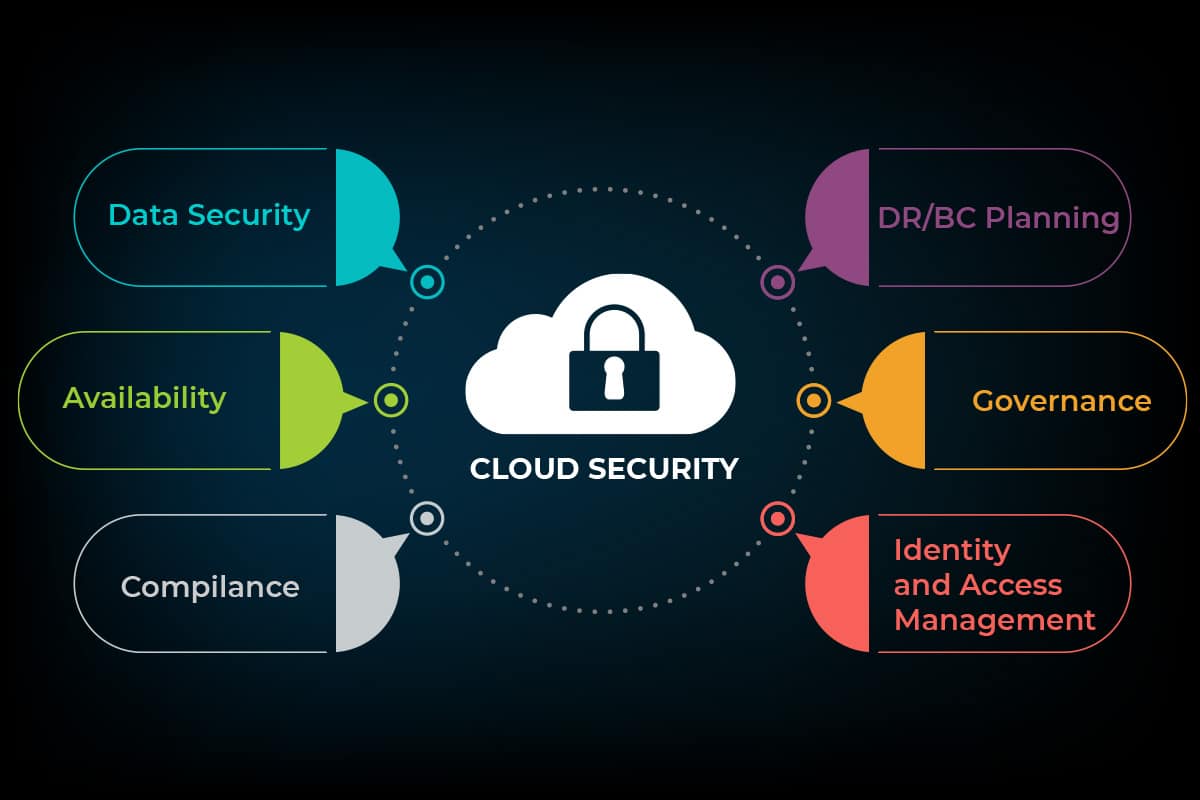
With high flexibility of specifications, you can choose any cloud computing solution to enhance capacity planning. In addition, it helps maintain business continuity and offers security with advanced technologies and controls.
The Importance of Cloud Computing in E-Commerce
Many people, perhaps you too, are asking themselves questions like, “Are cloud computing applications in e-commerce worth it?”. the answer is YES!
Keep reading, to clear your doubts regarding cloud computing applications in e-commerce businesses:
Scalability
Scalability entails that Cloud Computing applications bring elasticity, allowing you to cater to all your strengthening and increasing needs. All you will pay is WHAT YOU ARE USING; For example, controlling the services according to demand, traffic, and seasonal spikes.
Easy Accessibility
The e-commerce business usually spreads across cities, countries, and even continents. Here, your business must have cloud-based strategies. Having an e-commerce cloud will let you manage your extensive network of clients, customers, and partners remotely.
Cost Reduction
Cloud-based e-commerce applications not only offer all-time accessibility but also significantly cut down the costs, letting you use your hard-earned money on more important fronts. In addition, it enables you as a business leader to assess new-fangled opportunities without worrying about investing large amounts of money.
Redundancy
Do you know that by simply opting for cloud computing applications in e-commerce, you enjoy disaster tolerant services that also stay up to date?
For many e-commerce businesses, having high-quality, built-in redundancy within the cloud platform helps you guard your data from loss. Along with securing your data, it stays backed up.
Speed
No matter the category of your business, speed is important to satisfy the customer’s needs. If your site has experienced a sudden spike because of heavy customer traffic, the page loading will slow down, or the site gets unresponsive.
The solution is cloud computing. It offers you greater capacity, enhanced computational power, and amazing storage.
Picking a Cloud Computing Service for Your E-Commerce
IaaS (Infrastructure as a Service)
- Provides on-demand data storage
- Stores information on disks and high-end virtual servers
- Examples comprise cloud services presented by recognized brands, including Amazon and Microsoft
PaaS (Platform as a Service)
- Self-service portal
- A platform letting its customers develop and launch applications
- Ready-to-use cloud services infrastructure
- Examples: Google App Engine, Cloudy, and Cloud suite.
SaaS (Software as a Service)
- Third-party hosting service provider included in the loop giving access to the client.
- Pay-as-you-go basis
- Salesforce, NetSuite, and Slack
Bonus
- Magento with POWER8 is one of the most purchased and reliable options for e-commerce platforms. It’s designed to deliver high-level scalability and enhance performance. The key features are memory utilization, the ability to handle increased workloads and manage excessive data. It meets the fluctuating demands of all your customers.
- Cirrus is another option. It has an on open source platform. It helps e-commerce businesses to store massive data with its customization provisions. This platform provides an enhanced personalized experience by understanding the users’ behavior and needs.