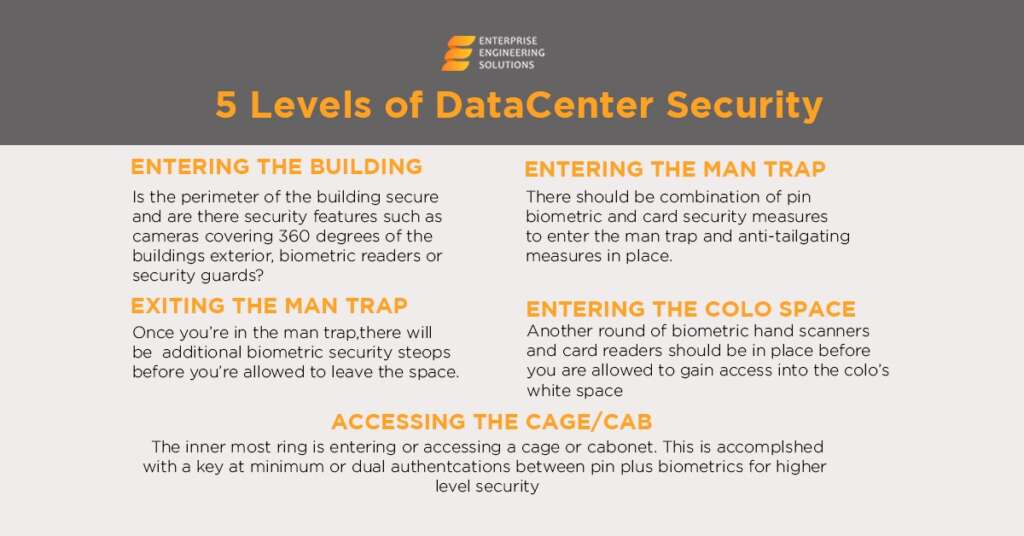
What Does a Data Center Technician Do?
The data center technician is typically equipped with the technical skills and talents required to complete this specific job within the organization. Datacenter technicians operate alongside network servers and hardware infrastructure to back up, maintain, and ensure a proper data flow within the network. The technician’s job may include improving data center security, running cables, and other maintenance services.
Knowledge of technology and technical requirements is a mandatory skill. A good data center technician must respond to questions from different sources and provide helpful information. Now in this blog, we will discuss Hiring the Best Data Center Talent.
What Skills Does a Good Data Center Technician Have?
Good data center technicians must be fluent with network infrastructure, operating systems, and various kinds of hardware deployment. Also, some roles may require advanced skills for a data center technician.
Typically, data center technicians must have competent Information Technology Consulting capabilities, including expert knowledge regarding switches, monitors, routers, and various infrastructure components. A technician must also have troubleshooting skills to perform tests and resolve network system problems.
Top Tips to Hiring the Best Data Center Talent

The different multi-disciplinary skills required to run a typical data center do not simplify hiring technicians. A data center must have practical support to maintain connectivity, the cloud, applications, Disaster Recovery, network appliances, virtualization, security, and storage.
This article underlines the critical qualities that a Chief Technology Officer (CTO) or infrastructure manager should consider when hiring the best data center talent/technicians.
- The best candidate for the role of Datacenter Technician must have a bachelor’s degree in Computer Science or IT Engineering. Also, training in hardware and software administration is an added advantage. Still, without regular education, a good data center technician must have at least one of these certifications:
- VMware Certified Professional 6 – Data Center Virtualization (VCP6-DCV)
- Cisco Certified Network Associate Data Center (CCNA Data Center)
- Cisco Certified Network Professional Data Center (CCNP Data Center)
- VCE Converged Infrastructure Administration Engineer (VCE-CIAE)
- Juniper Networks Certified Professional Data Center (JNCIP-DC)
- Depending on your business requirements and field, perhaps you may look for a specialist such as a networking specialist or a facilities technician. However, many businesses prefer generalists that can work with external contractors and vendors.
- Although studying to be a data center technician in College is rare, it is possible. For instance, some IT courses may contain a Data Center Technician course of study, offering an Introduction to Data Center Management Services.
- A Datacenter technician collaborates with business teams to ensure the well-being and uptime of the data centers. Infrastructure managers, operations engineers, and facility managers must have a reporting channel to collaborate effectively with the technician.
- A good data center technician must handle diverse responsibilities. Because technicians typically look over service level agreements, hardware, network connections, power infrastructure, software. The data center technicians you choose must know how to set up networking infrastructure and install it into racks and cabinets.
Some Businesses Prefer Someone Who Knows Structured Cabling and Security
- An excellent technician should work effectively with internal and external resources. The recruitment plan must include a strong sense of urgency to solve issues.
- The working hours through different shifts must cover 24/7, and someone should always be on-call. Hence, datacentre technician roles may require overnight or weekend operations coverage.
- Colocation data center technicians must express optimum professionalism when handling clients.
- To be effective, a data center technician must have the strength to move equipment (around 50lbs), with excellent verbal and written communication skills.
- As an employer, you also understand that many data center technicians regard their jobs as a stepping stone to other networking and virtualization career goals.
- Leverage the expertise of recruiting firms to scout different candidates and screen the right talent/technician for your business.
- Datacenter technician work benefits typically comprise long-term disability insurance, dental insurance, a 401 (k) plan, medical insurance, and bonuses. Perhaps you may also want to add life and vision insurance.
- Datacenter technicians may need to travel very often, sometimes without advanced notice. Therefore, ensure to pick a candidate with a flexible travel schedule that can integrate with your business’ requirements.