What is Cloud Security?
When talking about Cloud Security or Cloud Computing Security, the first thing you should know is “it’s a cyber-security discipline,” comprising a detailed and practicable set of policies that enlist all the essential technologies, advanced controls, and IT services protecting your personal and professional data and applications saved in cloud platforms.
It protects your information against threats, either internal or external.
Effective Cloud Security demands the hard work and efforts of every other person present in the company along with cloud providers and the customers that are using them.
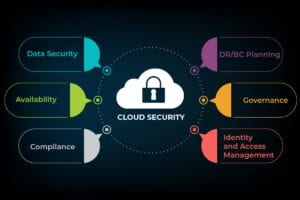
Primarily, cloud security comprises the below-mentioned categories:
- Data security
- IAM (Identity and access management)
- Governance (guidelines available on threat prevention, recognition, and mitigation)
- Data retention and business continuity planning
- Legal compliance
What Exactly Does Cloud Security Protect?
- Physical equipment required in networking, such as routers and cabling
- Operating systems
- Data servers
- Computing software used as a core of online networking
- Hard drives
- Computer virtualization frameworks, including both host and guest machines
- Runtime environments or running program
- Data (stored or modified)
- Applications
- E-mails
- End-user hardware such as PCs, smartphones, Internet of Things (IoT) devices, modems.
Cloud Computing Categories
- Public cloud services (run by the public cloud providers)
- Private cloud services (run by the public cloud providers/third party)
- Private cloud services (run by the internal team/staff)
- Hybrid cloud services (combined with private and public cloud computing configurations)
Why is Cloud Security Important?
- With the help of cloud security, you can centralize the company’s security infrastructure for enhanced protection
- Time to say goodbye to hardware
- Minimized capital expenditure helping you manage finances
- Limits the staff load and administrative overheads
- No need for manual security configurations
- Cloud computing services offer the ultimate dependability and reliability
- It is scalable as you are welcome to add additional features and offering access to as many users as you want without breaching your security
- It offers all-time visibility because everything integrates well. We can see security and other services talking to each other.
Potential Cloud Security Challenges
- The clouds are accessible by the team and devices outside the corporate network that are not supervised by IT compromising the all-time and extensive monitoring. This loophole can lead to cyber-attacks or information leaks.
- The chief risk of using the cloud is that there is no perimeter as all cloud environments seem exceedingly connected and account hijacks can get you into serious problems
- An employee with access to the cloud can go rogue exposing or exploiting the organization
- In a third-party cloud service provider’s situation, IT teams get extremely limited access and control over data and applications by default. Accessibility to fundamental physical infrastructure seems negligible.
- A Cloud-native breach appears pretty common, which is a sequence of cyber-attacks strategized by an antagonist based on the company’s errors and vulnerabilities. They simply transfer the data to their equipment without using malware to make this operation go undetected.
- The cloud providers can easily bypass your security controls letting them approach, access, and monitor your private details
- Human errors can cause misconfiguration of user access controls. Read more
Cloud Security Solutions
- The best approach is “encryption” imposed on communications and sensitive data.
- End-to-end encryption of the data uploaded on the cloud is a must
- Always change the default settings to not give the hacker a front-door access
- Always close the cloud storage bucket or else someone can open the URLs easily
- Make your primary passwords strong by mixing letters and figures with special characters. Go random!
- Choose a reliable password manager
- Don’t forget to back up your data that you have been regularly uploading on your clouds. It will help you restore or recover your data. You can keep the backup on your personal computer, external hard drive, or even a separate cloud.
- You must keep changing the cloud’s permissions after a certain period. It seems beneficial in preventing access to all the company’s data by any employee or device.
- Keep your ‘access all areas’ password only to yourself. Consider it your safe passage that must not permit usage to anyone, anytime.

Top Cloud Security Companies
- Qualys
- Check Point CloudGuard
- CloudPassage Halo
- Lacework
- Netskope
- RedLock by Palo Alto Networks
- Symantec Cloud Workload Protection
- Threat Stack Cloud Security platform
- Trend Micro Hybrid Cloud Security Solution





