Marketing, gaming, brand promotion, and entertainment are all areas where these technologies might be used. Individuals may be completely submerged in a virtual world via so-called virtual reality (VR) technology.
With Augmented Reality, the first step is usually to project or insert images onto the screen instead of starting with an accurate view of objects, such as through a cell phone camera. It’s easy to see why this is so appealing. It has developed innovative techniques to make its customers’ experiences even more dynamic and individualized to make them more fascinating.
Moreover, it’s also essential to illustrate how a product works if you’re in marketing. The jargon, on the other hand, might lead to misinterpretations.
How is Virtual Reality different from Augmented Reality?
Some examples of each will be shared.
What is a Virtual Reality Context?
Virtual reality is a computer-generated simulation of another planet or reality. 3D technology is used in movies and video games. You may create realistic simulations using computers and other sensory devices, such as headphones and gloves, by using a computer.
Virtual reality development services are being used for more than just entertainment for the first time. VR, in its totality, is the entire kind of VR.
The Concept of Augmented Reality

Augmented Reality (AR) is the ideal blend of digital and actual components for creating an artificial world. Blending digital components into the real world with AR technology (AR)!
For example, there will be score overlays and pop-up 3D images, text, and emails when watching a sports event on television.
Virtual Reality’s Operations are Being Explored
For the most part, virtual reality is focused on re-creating one’s visual perceptions. The user must wear virtual reality (VR) headset with a screen in front of their eyes. Because of this, communication with the natural world is completely broken. A pair of lenses separate the user’s view from the display in virtual reality. As the user’s eyes move and position themselves, so must their eyes.
In some instances, an HDMI connection may display the screen’s visuals on a computer or smartphone. Incorporating goggles, speakers, and even wearable technology may help create an immersive experience. This immersive nature of virtual reality is since it may be experienced via visual, auditory, and tactile cues.
How Does Augmented Reality Work?
AR utilizes computer vision, mapping, and depth sensing to display the user-relevant material. Cameras are used to provide digital content relevant to the user’s present look and may leverage this feature. Real-time digital material is added to the user’s actual surroundings in Augmented reality.
You may enjoy virtual and augmented reality services using smartphones or dedicated gear.
Evaluating VR and AR
VR and AR are two diverse forms of immersive technology.
| VR | AR |
| Simultaneous immersion into a virtual world | The system’s performance improves because of the addition of context. |
| In virtual reality, the system oversees controlling the user’s visual perception. | Real-world presence is guaranteed with augmented reality. |
| 25% of the actual world and a whopping 75% of virtual reality (VR) | AR comprises a virtual component of 25 percent and a fundamental component of 75 percent. |
| VR requires a connection of at least 50Mbps to immerse the spectator in action fully. | This amount of bandwidth is required for AR to be entirely immersive for the user. |
| Wearing virtual reality goggles is mandatory. | The use of an augmented reality headgear is entirely optional. |
| The user may fully immerse himself in a made-up world using virtual reality technology. | Using virtual reality technology, the user may fully immerse himself in a made-up world. |
| It’s a technique used in video games to enhance the player’s sense of immersion. | It’s beneficial in both the actual and virtual worlds. |
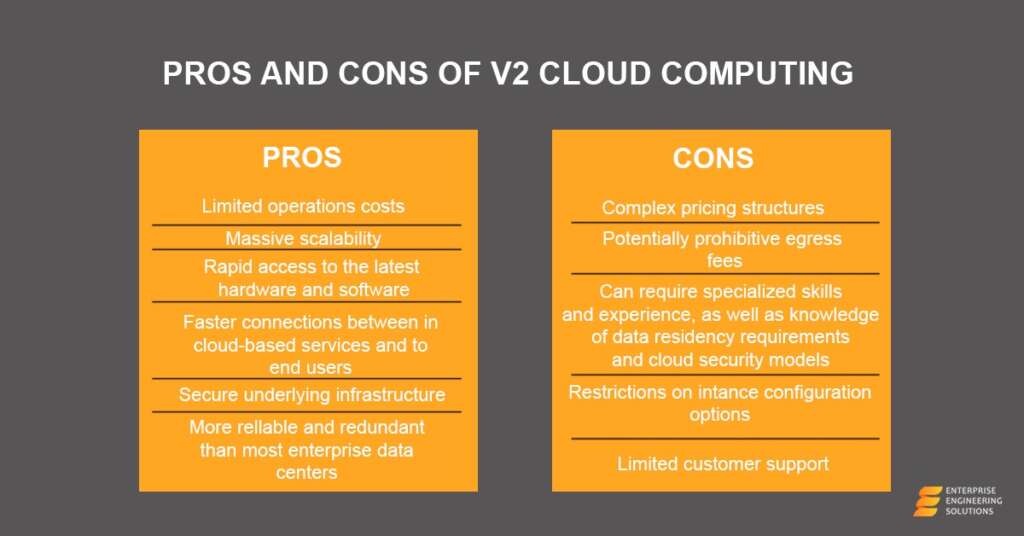
Virtual Reality’s Positive Aspects
The following are some of the advantages of virtual reality:
- Intuitive teaching.
- It is necessary to establish a setting that encourages participation.
- Make the most of your abilities at work.
- Make it easy for others to utilize.
- The ability to create a realistic world in which the user may go on quests is one of the critical advantages of VR.
- Teaching and learning may be more accessible and more pleasurable via virtual reality technology in the classroom.
Augmented Reality Positive Aspects
The following are some of the advantages of AR:
- Provides personalized education for each student.
- Motivating students to pursue their education
- Multiple fields of study to choose from
- There is a need for new ideas and ongoing improvement.
- Improvements in accuracy were made.
- It is possible to improve the user’s understanding of a subject matter by using augmented reality.
VR’s Negative Characteristic
The following are some of virtual reality’s detriments:
- Even if virtual reality (VR) becomes increasingly common, programmers will never be able to interact with it.
- Virtual reality is a constant source of escapism, and many individuals choose to spend their time there instead of confronting their difficulties in the real world.
- Real-world training and employment cannot be substituted by virtual training and jobs.
- According to this theory, a person’s ability to do well in a virtual reality environment does not guarantee that they will be successful in the real world.
AR’s Negative Characteristic
The following are some of AR’s detriments:
- The costs of AR technology implementation and development, as well as ongoing maintenance, are substantial.
- There is a slew of downsides to AR.
- Poor AR device performance is a potential problem that may arise during testing.
- The use of augmented reality may lead to mental health issues.
- The concept of augmented reality might be jeopardized if it is not adequately protected.
- Several major health issues, including an increased risk of eye illness and obesity, have been connected to excessive usage of augmented reality (AR) technology.
What is the Correlation Between VR and AR?
VR and AR cannot be used in isolation. Users may be transported into a fictional world when real and virtual worlds are merged in a single system. It’s a process known as interactivity.
Conclusion
Virtual reality and augmented reality are mirror images of one another in terms of their ambitions. Virtual reality creates a digital image of the world around us, while augmented reality inserts virtual elements into the real world. This technology is expected to be used by both consumers and businesses shortly.
Data may be intuitively interacted with rather than requiring screen-based effort. For these tasks, portable devices may be utilized instead of stationary equipment. Consolidated data has the advantage of being targetable at any time and from any location.