One of the questions is to initiate “what is a data center security levels,” and the answer is that “it is the combination of servers placed on the central point where most of the critical applications of organizations are hosted.” Datacenter design is based on network, storage devices, and shared applications.
The major components of the data center are switches, servers, firewalls, storage devices, and APIs. One of the significant duties of data centers is to store confidential and sensitive data of public or private sector organizations as per the organization’s requirement.
Data Center Security Levels
Different digital hazards exist globally, like physical, technical, and environmental. And that is why various organizations prefer data centers to store sensitive data.
An earthquake is one example of a natural disaster that can do massive damage to your crucial information. So, different types of security are applied to a particular organization, such as physical and technical.
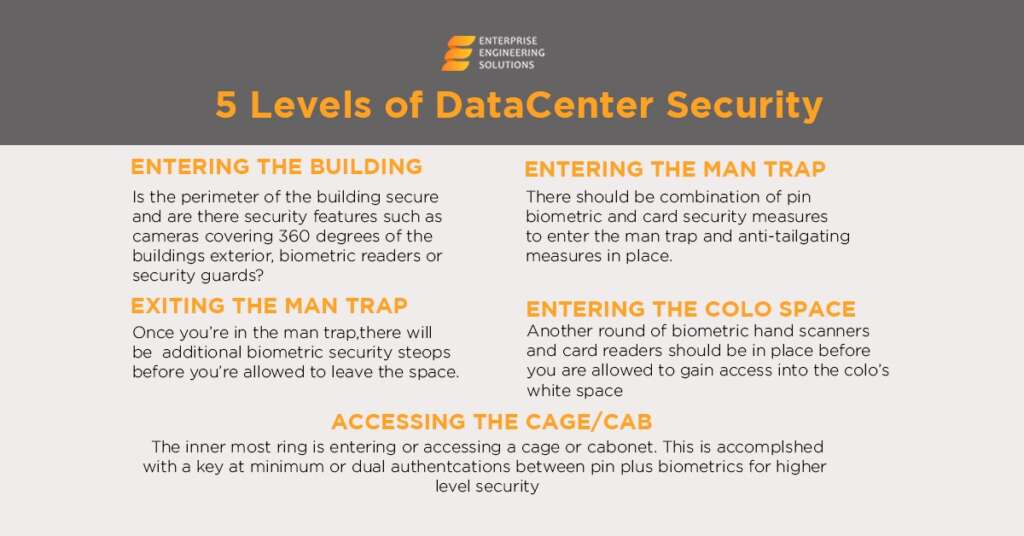
Multiple levels of security can apply to the data center to secure the data of different organizations. In the data center, four different levels of protection are applied for securing the data. The security level is called tier and “level of service.” The data center security levels are defined as:
- Tier 1
- Tier 2
- Tier 3
- Tier 4
Physical Security
This comes on the pretty upper notch of the data center security levels. Physical security is an integral part of an organization that is used to secure a particular area of the organization physically. People think security is the name for applying locks, alarms, bars, sprinkle systems, and security guards.
If we see the slandered ISO27001, then physical security is a complete and major component of an organization that can apply to the data center. Physical security plays an essential role in functional organization.
Protection of building, equipment, and critical organization data is the major component. Different physical threats exist on the earth like natural events, several environmental conditions, intentional acts, and unintentional acts. On behalf of such types of threats, different organizations must comply with risk management. Risk management is the method that helps to identify various vulnerabilities of the organization.
Talking about the data center security levels, physical security involves safeguarding building sites in such a way that asset theft and loss are minimized. Building construction, room assignments, emergency protocols, equipment installation and use restrictions, power supply, product handling, and linkages with other contractors and agencies are all things to think about. It spots the probable intrusion and then alerts the relevant person.
Secure Your Building
The data center should be constructed of materials that can withstand natural disasters such as hurricanes, tornadoes, and flooding from nearby water sources. A data center, for example, should not be situated in an area prone to earthquakes or volcanic activity.
The switch is a Nevada-based company with Reno and Las Vegas locations that hold government and commercial data. Nevada has a low risk of natural disasters, making it a suitable site for a secure data center.
To maintain the data center security levels, a data center should be kept out of sight from adjacent industrial facilities. A data center can sometimes be hidden in a natural location, such as dense woods or mountain ranges.
Consider a simple grey concrete structure bordered on one side by a dense forest of towering trees and the other by a mountain range. A casual observer might miss it. A difficult-to-pass-through wall or metal fence should encircle a data center to protect the physical facility.
The facility should be protected by substantial concrete barriers to protect it against physical attacks such as explosives. Windows are pointless because they allow for unauthorized entry. Some portions of the structure require doors for fire safety, although they should only be utilized as an escape route. Alarms and cameras pointed at the entrance from both the inside and outside the structure should be put on fire doors.
Technical Security
Layered security mechanisms for the actual data sent on the servers in the facility should be included in data centers. There are several tiers of security codes that may be used, Data encryption, Network filtering, User authentication, and Security analysis. This is also one of the highlighted parts of the data center security levels.
User Authentication
User authentication for network access should be a two-step procedure at the very least. Inputting a password should be the initial step. The second phase includes obtaining admission by using a token that confirms a user’s specific possession. Both the password and the token must be entered accurately by the user.
Data Encryption
Data encryption encrypts information, preventing unauthorized persons from accessing or altering it. On the servers, a firewall might provide extra protection.
Network Filtering
Network filtering is a technique that may be applied to routers and firewalls to prevent an attack before an unauthorized user tries to log in. An individual attempting to access the network from a public where harmful behavior is likely to occur will be immediately prevented by network filtering.
Security Analytics
Organizations that integrate sensitive data might benefit significantly from security analytics. The tracking, identification, and alerting of potential risks are all part of analytics. Security analytics make the system continually watched.
Moreover, the suspicious behavior is analyzed to identify the bizarre patterns. Suspicious logins or numerous attempts to log on within a particular time range are examples of unusual behavior. For example, an iPhone will automatically lock after a specific amount of unsuccessful login attempts as a security mechanism, deeming this suspicious behavior.
The efficient application of analytical software can help identify an unexpected change in the configuration of a server. Analytics is a helpful tool for protecting against assaults since it may be pretty accurate in detecting risks.





