Machine learning is a form of artificial intelligence. Machine learning uses historical data to make future predictions and trends. Machine learning uses data to make future predictions automatically.
What is Machine learning as a Service?
Machine Learning as a Service is a cloud-based service that provides users with the tools to use Machine learning to the advantage of their businesses. Machine learning as a service (MLaaS) provides a pack of machine learning tools for the users who can use them at a specific price. It helps its users with:
- Predictive analysis for original use cases,
- model deployment,
- preprocessing of data,
- run orchestration,
- training, and tuning of models.
The idea of making computers teach themselves how to perform tasks is what we call machine learning. It is a form of artificial intelligence. Machine learning includes deep learning and neural networks in big data. So, Machine learning stands apart from conventional programming as the Machine learns all by itself instead of doing what we program it to do. We are the modern ML experts delivering digital solutions and machine learning consulting services to design and develop computer programs with the power to acquire and comprehend instructions without being programmed.
Users provide extensive data sets to the Machine, and it automatically figures out valuable and vital data. Machine Learning as a Service software tool can perform face recognition, regression to speech recognition, trend prediction, predictive analysis, and computer vision. MLaaS solves various problems like healthcare automation, IoT, and much more.
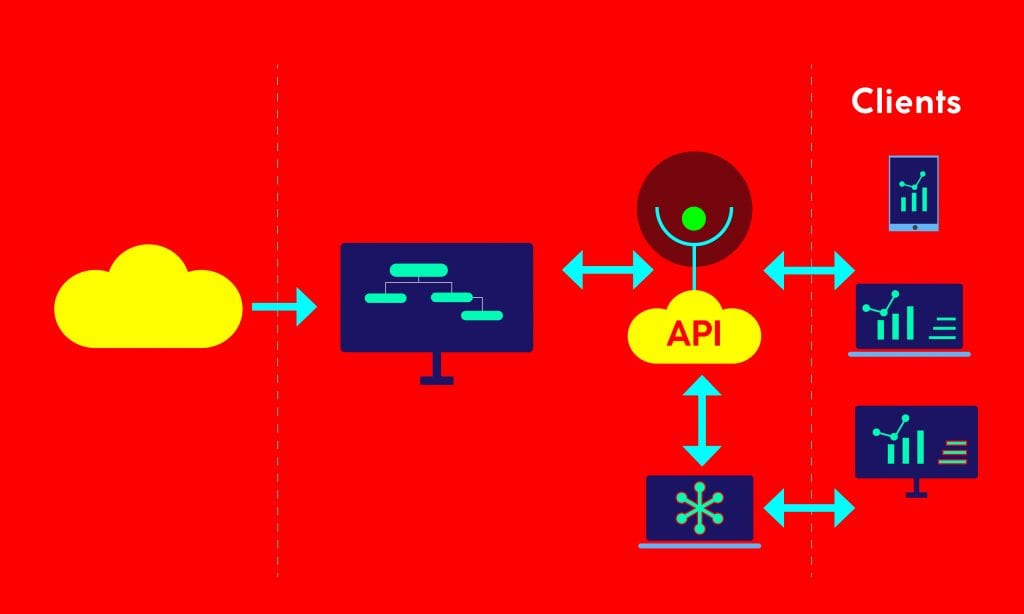
How Does Machine learning as a Service Work?
Many Platforms Provide Machine Learning as a Service (MLaaS).
Machine Learning tools are cloud-based and offered by cloud service providers like Microsoft Azure ML, Google Cloud ML, Amazon Sagemaker, IBM Watson ML, and many more. Using machine learning as a service (MLaaS) is pretty easy, especially with the help of these ML platforms. The tools support artificial intelligence-related tasks, machine learning algorithms, training and tuning, data visualization, facial recognition, natural language preprocessing, and predictive analysis.
A user only pays for what they need. Machine learning as a service (MLaaS) offers many categories to work.
The following are some of the popular categories used on Machine Learning platforms:
- Forecasting
- Data exploration
- Anomaly detection
- Natural language processing
- Trend analysis and prediction
- Searching of datasets
- Understanding of datasets
Machine learning as a service makes it easier to work with machine learning algorithms. It simplifies choosing datasets and models to train the Machine. Without MLaaS, these tasks would have been very hectic, for example, working with complex programming like python, IDE, using APIs, and libraries. It would also require an expert in data science or cloud computing to fulfill more manageable use tasks (MLaaS).
To use machine learning as a service (MLaaS), go to the platforms mentioned above and choose the service you want. Each cloud platform provides a variety of tools and services. Choose the services suitable for your desired task, and you are ready.
The Future of Machine Learning as a Service
Machine learning is a new technology widely adopted by many notable companies like Facebook, Uber, Google, etc. These companies use machine learning to better understand their customers’ wants by analyzing data to generate intuitive insight. Machine learning has increased the profit of many companies, and this technology will continue to develop.
We expect the global machine learning market to increase from $7.3 Billion in 2020 to $30.6 Billion in 2024. It means that the machine learning market will grow at a 43% annual rate. It is tough to train machine models from scratch, and MLaaS helps solve this issue. You don’t need to begin from scratch because machine learning as a service automates many required procedures to train a machine and manage its deployment.
Suppose you don’t employ Machine Learning as a Service. Trained machine learning models get deployed on your company servers. MLaaS makes it easier to train, manage, and deploy ML models. It makes it easier to work with machine learning algorithms. It simplifies choosing datasets and models to train the Machine.
Conclusion
Machine learning as a service (MLaaS) is very cost-effective and cost-efficient. Machine learning as a service (MLaaS) is constantly helping businesses to flourish and excel. Machine learning as a service (MLaaS) is assisting companies in competing in the advancements of technology. It is immense and yet to get explored fully as research and work are still ongoing to discover the full potential of machine learning.
This industry is growing at an exponential rate. The field of machine learning is developing and snowballing, as there is still a lot to discover. The number of (MLaaS) platforms is expected to increase. Including the existing tools they offer.