Amazon Web Services (AWS) provides the tools for a broad range of applications, AWS is a scalable cloud computing platform for maximum stability and performance. AWS needs to safeguard your systems and information’s confidentiality, integrity, and availability and preserve your trust and security.
AWS can automate manual safety chores to concentrate on the growth and innovation of your company. Moreover, you pay for the services you utilize. All clients benefit from AWS as the only commercial club scrutinized and recognized as secure enough for top secrete workloads with its services and accompanying supply chain.
The following description of AWS security processes should give you basic knowledge of the AWS capabilities to secure your data.
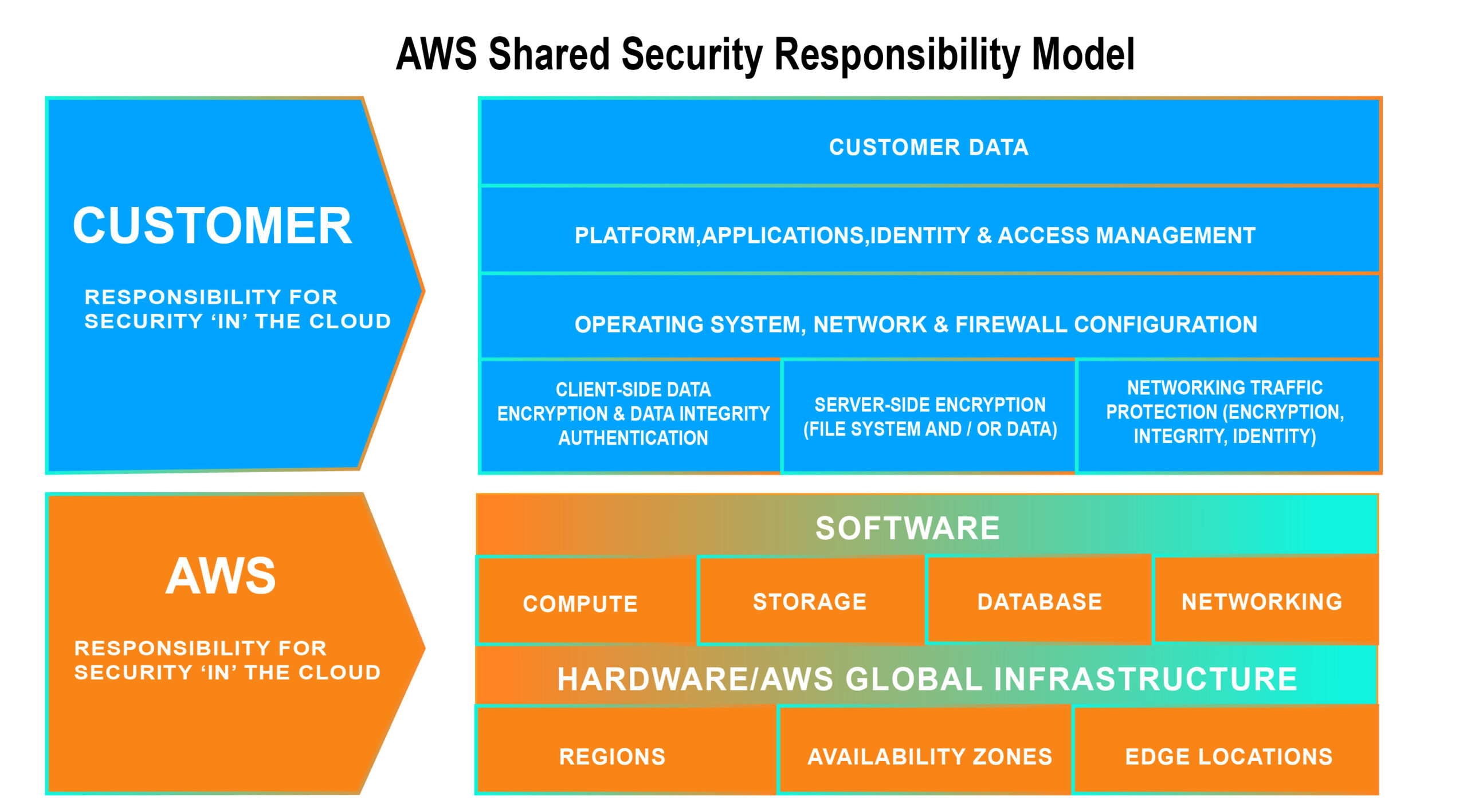
AWS Shared Responsibility Model
The AWS architecture was designed to be one of today’s most adaptable and safe cloud computing systems. It is meant to provide a highly scalable and dependable platform for clients to deploy apps and data swiftly and securely.
This infrastructure is created and managed according to best practices and standards for security and considers the unique demands of the cloud. To guarantee that the underlying infrastructure is monitored and secured 24×7, AWS utilizes redundant layer controls, constant validation, testing, and a significant level of automation. In each new data center or service, AWS guarantees that these controls are duplicated.
The data center and architecture created to meet the requirements of our most security-sensitive clients is used for all AWS customers. So, you have a durable and secure infrastructure without the capital spending and operating overhead of a typical data center.
AWS Security Tools Overview
AWS offers its customers a range of security methods. First and foremost, the organization provides comprehensive coverage and infrastructure protection. Secondly, different safety procedures have been included for each AWS service. A short overview of the various tools is provided below.
- AWS Config: This inventory of resources allows customers to check and report changes to their settings on their configuration history.
- Key Management Service: Edit and manage data protection keys for various services. You may also encrypt your data using this service if, for example, you wish to preserve better security in Amazon cloud storage.
- CloudTrail: This program tracks the use and access of your account and notifies you about any changes, as does its name.
Identify and Access Manager creates various users and groups that access AWS clouds. You may use it for all instances to establish your passwords, key codes, MFA, and IAM. In addition, reports and warnings will be supplied if they are changed. - A trusted consultant is an advice service that shows how you may adjust performance, improve safety, and maximize usage expenses.
- CloudWatch: Controls the utilization of Amazon infrastructure resources and apps.
Can We Rely on Default Security Settings?
AWS may not be sufficient, even if it has excellent standard safety specifications. Users should be aware that these settings typically need to be customized for more secure, sensitive information.
Many Amazon cloud violations arise through overuse, obsolete, and robbery. AWS Identity and Access Management Tools are therefore essential. This allows you to create unique, accessible users and groups.
Although AWS does have excellent default safety settings, they may not be sufficient. Users should know that they may often need to change such settings for increased protection, sensitive data.
Much of the Amazon cloud security breaches arise through misuses, obsolete access credentials, and stolen access. The adoption of AWS Identity and Access Management (IAM) solutions is therefore crucial. Through this, individual users and groups with a special permit may be established.
The open S3 seals, which have too much access by too many, are another vital source of breaches. These are rich hacking paths. Closing the buckets using AWS help (e.g., AWS Policy Generator and Block Public Access). For both read and write access, setlists of access controls. To secure your data, utilize encryption.
Further insight is accessible through the whitepaper developed by the Amazon team about AWS security processes. This article describes how frequently Amazon cloud security problems may be mitigated and how different security procedures may be more closely reviewed.
Finally, do not forget that members of your IT staff may earn Amazon cloud security certifications. It provides a range of training programs, including security, advanced networking, DevOps engineering, and cloud development (from 6 to 2 months). They cover several vertical areas.




![Cybersecurity Laws And Regulations In US [2023] 4 Cybersecurity Laws And Regulations In US](https://www.eescorporation.com/wp-content/uploads/2023/02/4-1.png)

