Customers may now buy products and services from the comfort of their own homes without having to travel to a bank. All thanks to the growing popularity of online businesses. Data security is critical in today’s world, as cybercriminals aggressively steal private and sensitive information. This article explains how to set up and protect your servers.
Follow these steps before deploying a server in a live environment to assure its safety. Although each Linux distribution is distinct, the underlying concept is essentially the same. As a result of completing this configuration, your servers will be well-protected against common security threats.
Companies are welcome to benefit themselves with our data center networking solutions for creating stable connections between data centers and external/connected devices, effortless communication, and safe information exchange.
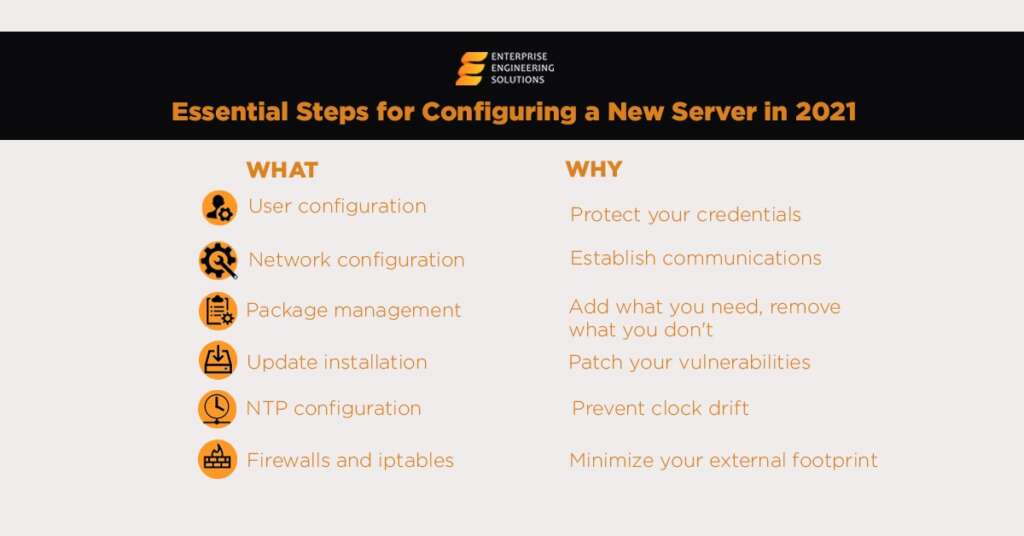
Tips for Servers Configuration
Setting Up the Internet Protocol (IP)
So that it can establish an internet connection, you must first provide the server with an IP address and hostname. The majority of servers will need you to use a static IP address to ensure that customers may access the resource from a consistent location. Consider how isolated the server’s segment is and where it belongs in the broader network structure if your network uses VLANs.
If you do not require IPv6, turn it off. Name, domain, and DNS server information for the server configuration should all be specified with care. “nslookup (Unix-like operating system command)” should be used to verify that name resolution is working correctly across two or more DNS servers. It is the best tip you can get for servers configuration.
Preferences for The User
You must first update the root password on the server before proceeding further. Your password should include a combination of upper- and lowercase letters as well as numbers, symbols, and punctuation characters. The history, locking, and complexity requirements of an account used locally may be compromised if the password does not include at least eight characters. Users that want higher rights should be given sudo access means as means a substitute user instead of relying on the root user.
Packages
Install any extra software you will need that is not included in the distribution while you are setting up a server, for whatever reason. PHP, NGINX, MongoDB, and various supporting tools like pear are among the most often used software packages. A smaller server footprint will eliminate no longer needed software, and hence, deleting unneeded packages from your server will be beneficial for efficient performance. If you need their specialized services again shortly, it will be easy to reinstall them using your distribution’s package management system. Absolutely a marvelous pick for servers configuration!
Firewalls and iptables
Even if the default iptables setup does not open the ports you need, it is always a good idea to double-check the settings to make sure they are proper. In order to keep your server running well, you should only open essential ports. Consider blocking all except the most critical traffic if a firewall protects your server. Even if your iptables/firewall is configured to be limited by default, remember to open up everything your server configuration needs.
Installation and Configuration
Double-check to see if any of the server’s installed packages must be updated. As a result, it is critical to keep up with the latest kernel and default software. Earlier versions may be used if necessary, but we recommend using the most current version since it is more secure. An automatic update mechanism is offered for individuals who like to keep their software current.
After installing the necessary packages, you must maintain your server’s software up to date. Everything you have added, including the kernel and any pre-configured settings. Always use the most current production release to keep your system secure. The most current version supported by your package management system will be provided in the vast majority of circumstances. You should set up automatic updates in the package management tool for the services you host on this server.
Setting Up the NTP Protocol
Your server’s time may be synchronized using an NTP server. It is up to you whether or not you want to utilize an external NTP time server accessible to everyone. The most important thing is to maintain the server clock from drifting away from the actual time. Authentication problems may arise due to the time skew between servers and the infrastructure that authenticates them, for example. Even though it seems simple, this critical infrastructure must be carefully cared for.
Increase SSH Security for Servers Configuration
In the same way that Windows has a command-line interface, Linux also has one. SSH is a popular method of logging into Linux systems for administrative purposes. As a security precaution, make sure that limiting SSH access for the root user prevents remote exploits.
Additionally, you may restrict access to certain IP addresses if a specific set of users or clients use your server. Changing the default SSH port number is possible to protect yourself from hackers and criminals, but this is not as secure as you think since a simple scan might show your open port. The configuration of a server is not as complex as you may think, but it does need much attention to detail to provide the highest level of security. Using certificate-based authentication and disabling password authentication are the best ways to guard against SSH exploits.
Daemon Setup and Configuration
Once you have deleted all of your packages, make sure you have the necessary applications set to start automatically when you reboot. To avoid needless daemons, be sure to deactivate them. Reduce the server’s active footprint as much as possible, leaving just the attack surface areas required by the application (s). All remaining services should be hardened as much as possible to ensure long-term stability.
Protecting Your System with SELinux and Other Tools
Secure Linux (Security-Enhanced Linux) is a hardening tool for the Linux kernel that gives administrators more control over who may access their servers. It is the real-world implementation of SELinux, Secure Linux (SELinux). Please use the status utility to determine whether your system is running SELinux. You are safe if you get a notification saying that SELinux is guarding your data. Strictly speaking, the word “disable” means that SELinux is no longer active and no longer safeguarding you related to servers configuration.
Linux distributions, for example, rely on MAC (Mandatory Access Control). It is an excellent defense against unauthorized access to your computer’s resources. It is a good idea to test your settings with SELinux enabled to ensure that nothing legitimate is being blocked. Other applications like MySQL and Apache may be fortified in various ways.
Logging
Before installing the program, be sure that the logging level you need is enabled and have the resources to handle it. Creating the logging structure, you will need to troubleshoot this server is an excellent time to start now. Most applications allow for custom logging settings, but striking the right balance between too little and too much data may require experimentation. Many third-party logging systems exist that may help with anything from data aggregation to data presentation, but each environment’s needs must be considered first and foremost. Afterward, you will be in a better position to locate the required gear.
In the beginning, it may take some time to apply these procedures. An initial server setup strategy should be established to ensure the long-term viability of new computers in your environment. The consequences of not taking any of these steps if your server is ever attacked might be disastrous. Even if a data breach does occur, it will be far more difficult for hackers to get your personal information if you follow these recommendations.
Conclusion
Making a lapse in these safeguards might put your server in more danger if attacked. This does not ensure safety, but it does make the process more difficult for hostile actors and demands more significant experience in the face of these dangers. It would help if you were well-versed in data breach prevention to leave no openings for cybercriminals.





