This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
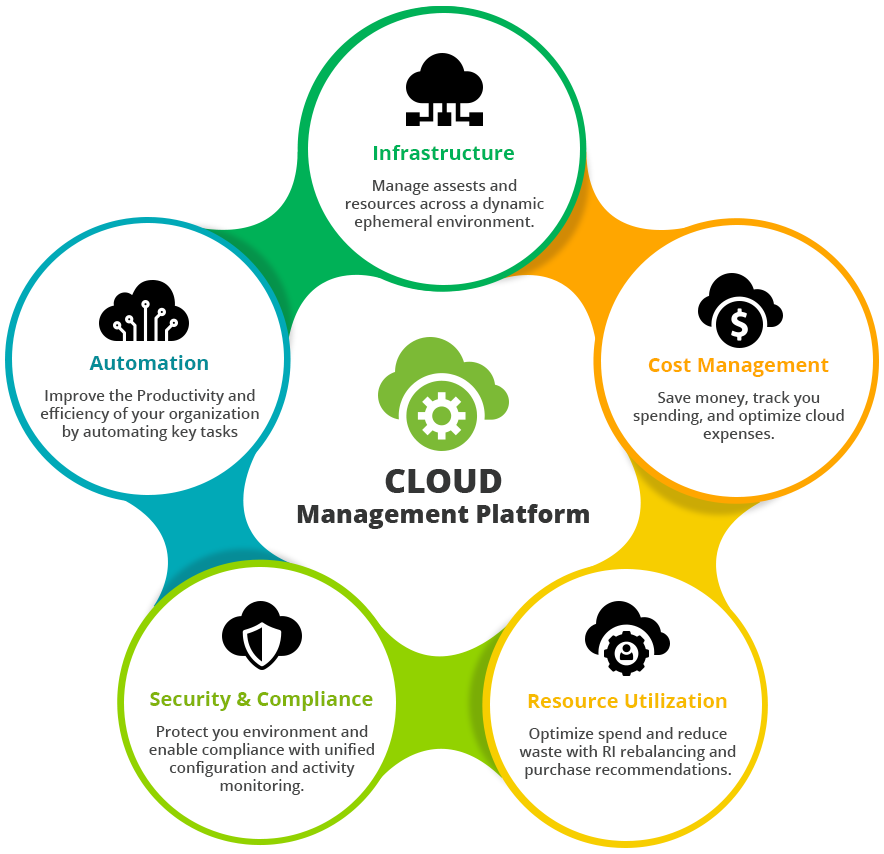
Cloud Computing
Mainframe vs. Server: How Are They Different?

Cloud Computing
DevOps As A Service AWS
Artificial Intelligence
How AI can Improve Cloud Computing?
Cloud Computing
What are the Characteristics of Big Data?

Cloud Computing
Top 5 Big Data Challenges

Cloud Computing
Capgemini vs Deloitte: Which is best for cloud services?

Cloud Computing
Cloud Readiness Assessment: A Comprehensive Guide

Cloud Computing
What is Disaster Recovery in Cloud Computing?

Cloud Computing
V2Cloud Review: Pros, Cons and Alternatives

Cloud Computing
Cloud Performance Testing: A Comprehensive Understanding

Cloud Computing
Openstack VS CloudStack: Comparing Similarities and Differences

Cloud Computing
Business Agility in Cloud Computing

Digital Marketing
Cloud Computing for Marketing: How the cloud helps marketers in 2022?

Internet Technology
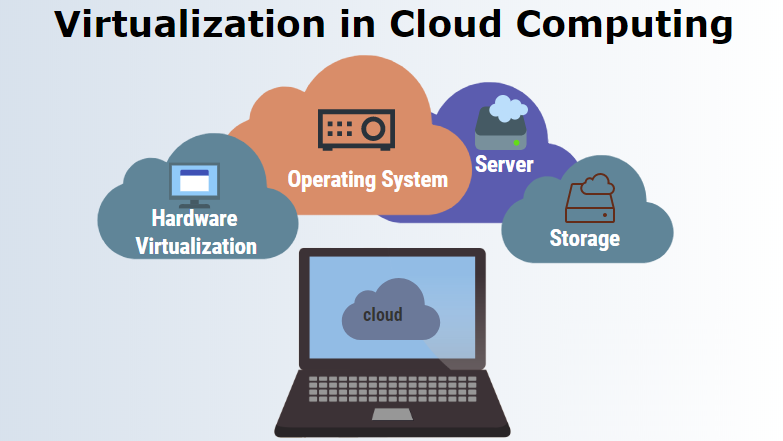
What is virtualization in cloud computing?
Cloud Computing
Cloud Computing and SEO Impacts
Internet Technology
What is the Cloud Computing Performance Metrics in 2022?

Cloud Computing
Deloitte vs PwC Comparing Cloud Services and Consulting

Internet Technology
Cloud Forensics Basic Concepts and Tools in 2022
Cloud Computing
Accounting for Cloud Computing Arrangements

Cloud Computing
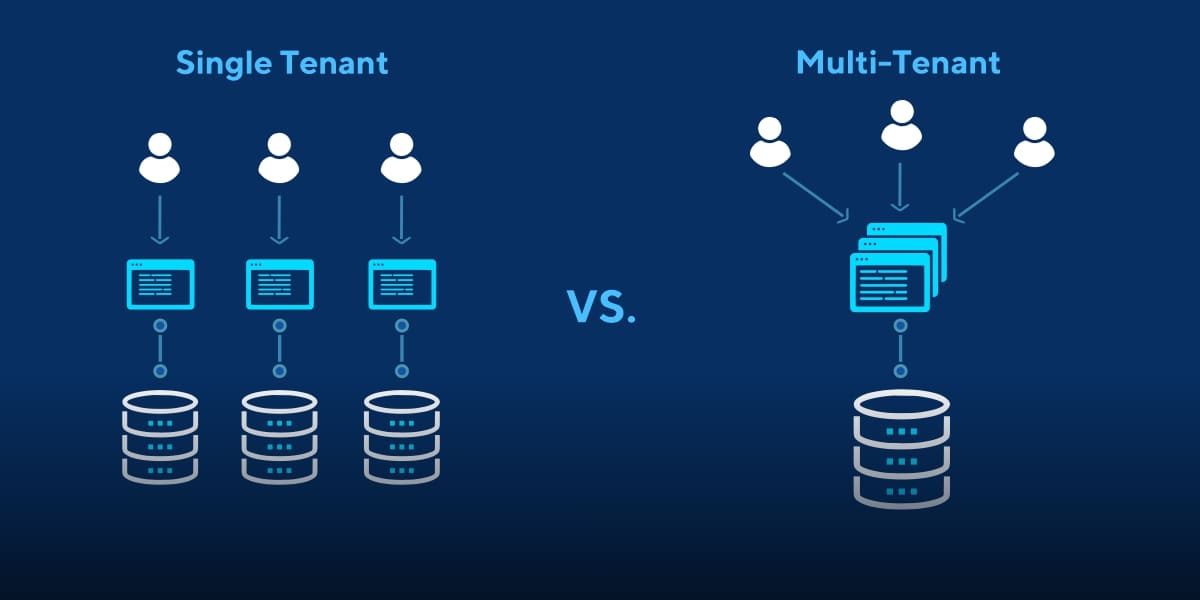
Important Multi-Tenancy Issues in Cloud Computing
Cloud Computing
What Is Lift And Shift Cloud Migration?

Internet Technology
Top 10 Best Cloud Gaming Services of 2022

Internet Technology
Best Cloud Security Tools in 2022

Internet Technology
Alibaba Cloud vs AWS: A Comprehensive Comparison [2022]
![Alibaba Cloud vs AWS: A Comprehensive Comparison [2022] 27 Alibaba cloud vs aws](https://www.eescorporation.com/wp-content/uploads/2021/09/Alibaba-Cloud-vs-AWS-Comparison.jpg)
Cloud Computing
Cloud Dev Environments: Best Cloud IDEs in 2022

Cloud Computing
Deloitte vs Cognizant: Consulting and Services Comparison 2022
Cloud Computing
How to Improve AWS Cost Optimization in 2022?

Cloud Computing
What legal issues in cloud computing could have to face?
Cloud Computing
Personal Cloud Computing: Why should one have a personal cloud?

Cloud Computing
What will Happen if there is No Cloud Computing ?

Cloud Computing
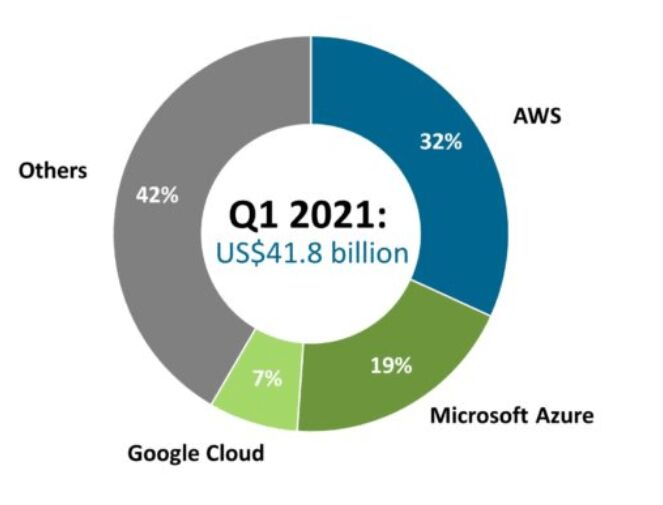
Public cloud market share statistics in 2022
Cloud Computing
Cloud computing optimization: Why is it important?

Cloud Computing
Infosys Vs. Accenture: Working and Cloud Services Compared
Cloud Computing
Migrating e-commerce to cloud: Benefits, And Tips

Cloud Computing
Cloud computing in Robotics: How is Cloud Empowering Robotics?
Cloud Computing
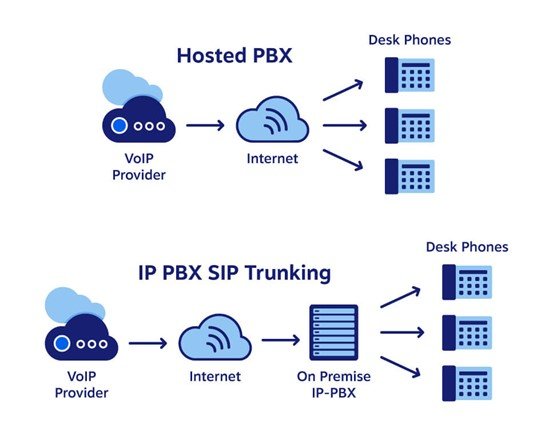
What is Cloud PBX and How does it work?
Cloud Computing
Cloud Native Computing vs Cloud Computing

Cloud Computing
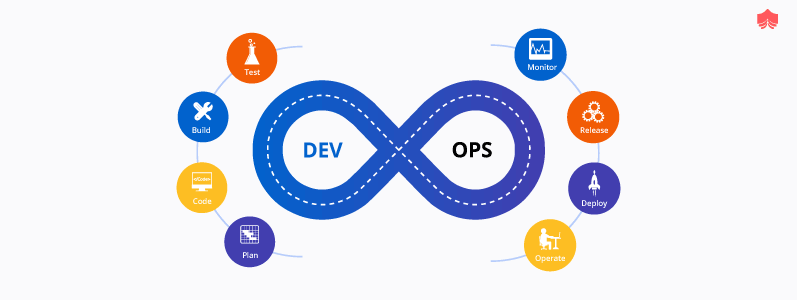
Best Practices For Effective DevOps In The Cloud
Cloud Computing
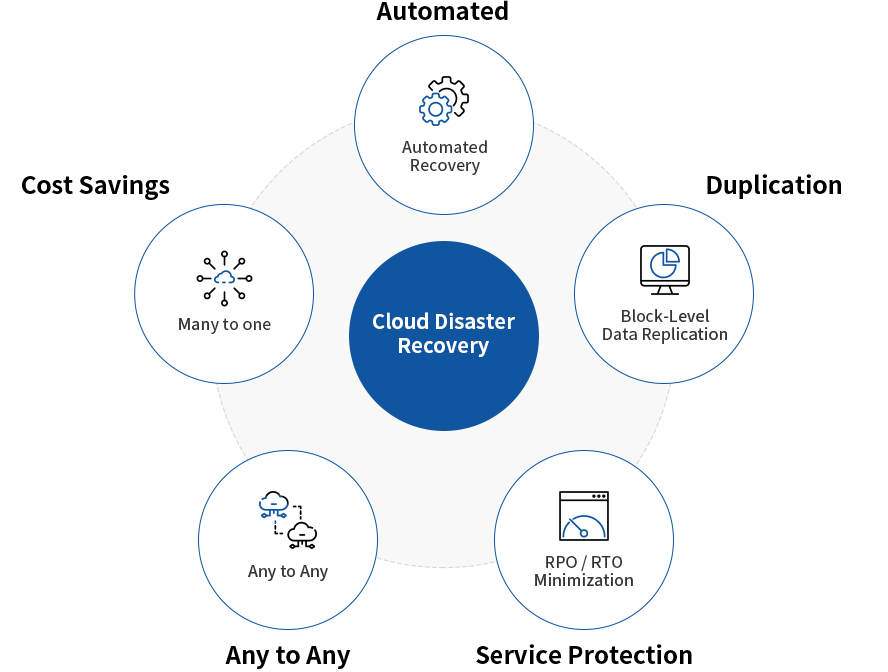
Cloud Disaster Recovery Best Practices
Cloud Computing
The Need of Cloud Computing Applications in the Banking Industry

Internet Technology
Amazon Web Services : Best Security Tools 2022
Internet Technology
COVID-19 and Cloud Computing: 7 Important Business Benefits on Healthcare

Internet Technology
What Is The Difference Between A Data Center And Cloud Computing?

Internet Technology
Cloud Storage Vs Cloud Computing: What’s the Difference?
Cloud Computing
How Much Does Cloud Computing Cost?
Cloud Computing
Cloud-based Organizations are Managing Better in COVID-19

Internet Technology
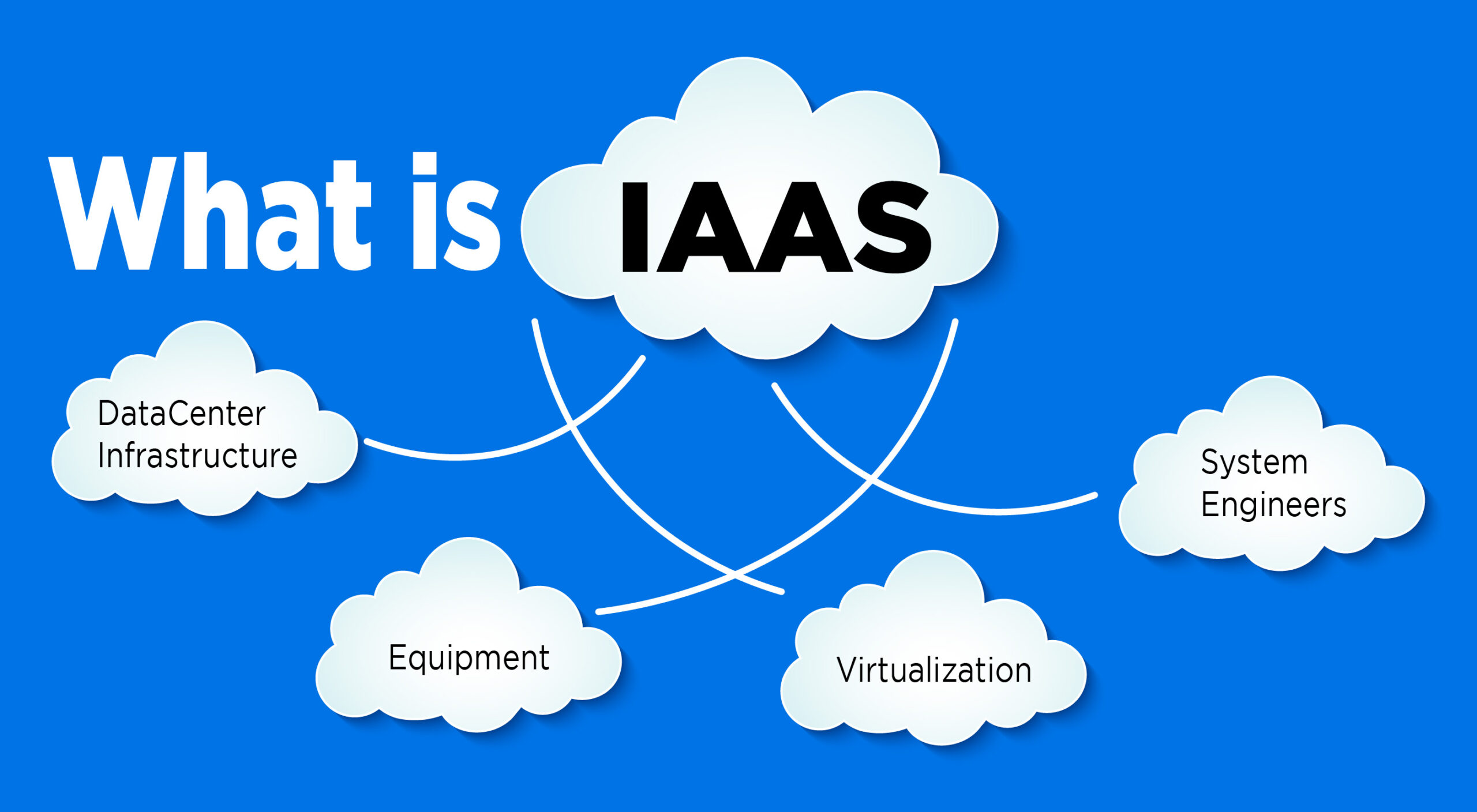
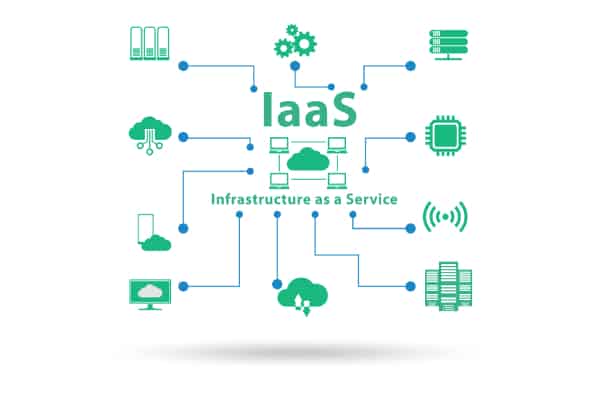
Infrastructure as a Service Use Cases: 6 Powerful Business Attributes
Cloud Computing
10 Cloud Computing Applications in 2022
Cloud Computing
Best Amazon Storage Services and its Advantages

Cloud Computing
Limitations of Cloud Computing and its 5 Disadvantages

Internet Technology
Cloud Storage Benefits: Helping You Increase Productivity in 2022
Internet Technology
Cloud security – A Detailed guide
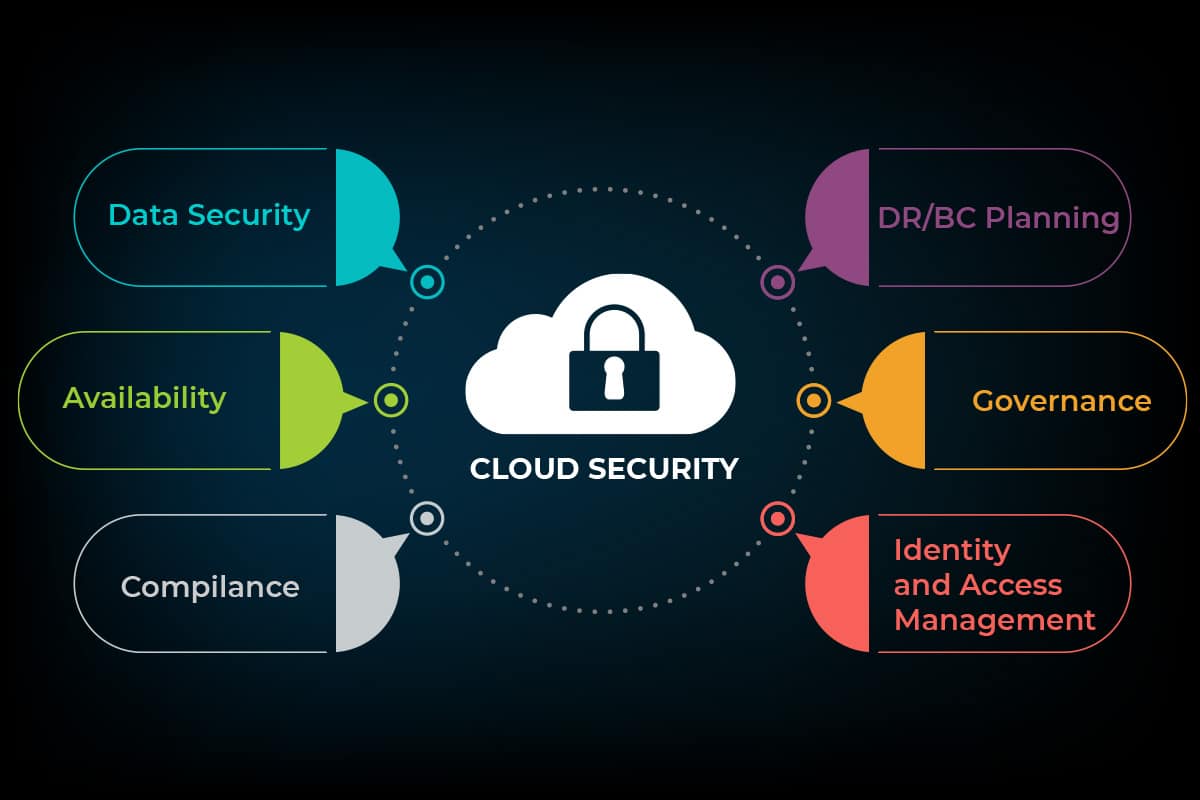
Internet Technology
Public Cloud in 2022: Understanding The Benefits and Disadvantages

Internet Technology
Amazon Web Services: The 3 Storage Solutions Driving Cloud Services
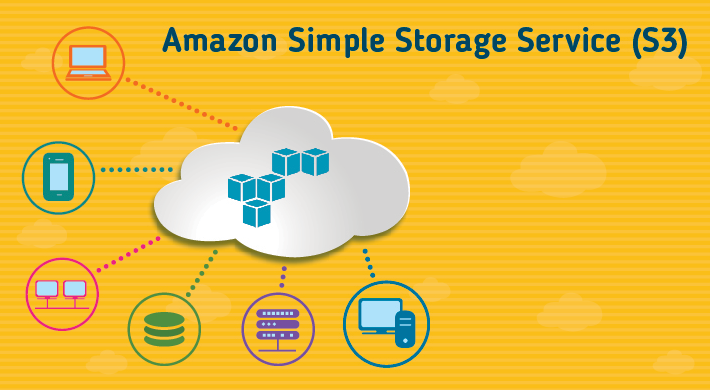
Internet Technology
Why You Should Choose Google Cloud Computing Services vs AWS

Cloud Computing
35+ Cloud Computing Statistics, Facts & Trends for 2022

Internet Technology
Public Cloud vs Private Cloud – A Comprehensive Comparison

Cloud Computing
5 Best Cloud Computing Services Companies in 2022

Cloud Computing
Cloud Computing Overview – Defining a New Era of Technology

Cloud Computing
Cloud computing applications in agriculture

Cybersecurity
How to Detect and Prevent Email Security Risks in 2023?

Cybersecurity
Cybersecurity Laws And Regulations In US [2023]
![Cybersecurity Laws And Regulations In US [2023] 77 Cybersecurity Laws And Regulations In US](https://www.eescorporation.com/wp-content/uploads/2023/02/4-1.png)
Artificial Intelligence
How to Use AI and Machine Learning for Cyber Security?

Cybersecurity
Mitigating Mobile Malware Attacks with MDM

Cybersecurity
What are NYDFS Cybersecurity Regulations?

Cybersecurity
Types of Security Controls

Internet Technology
Network Security Policy: A Definitive Guide
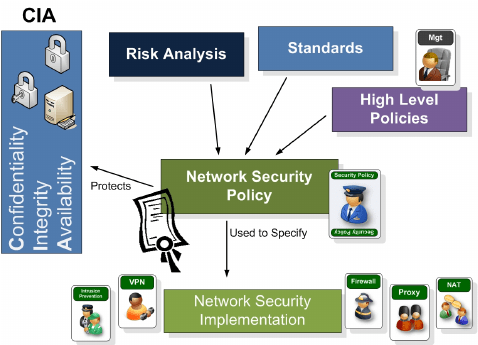
Cybersecurity
Shared Responsibility Model In Cloud Security Explained
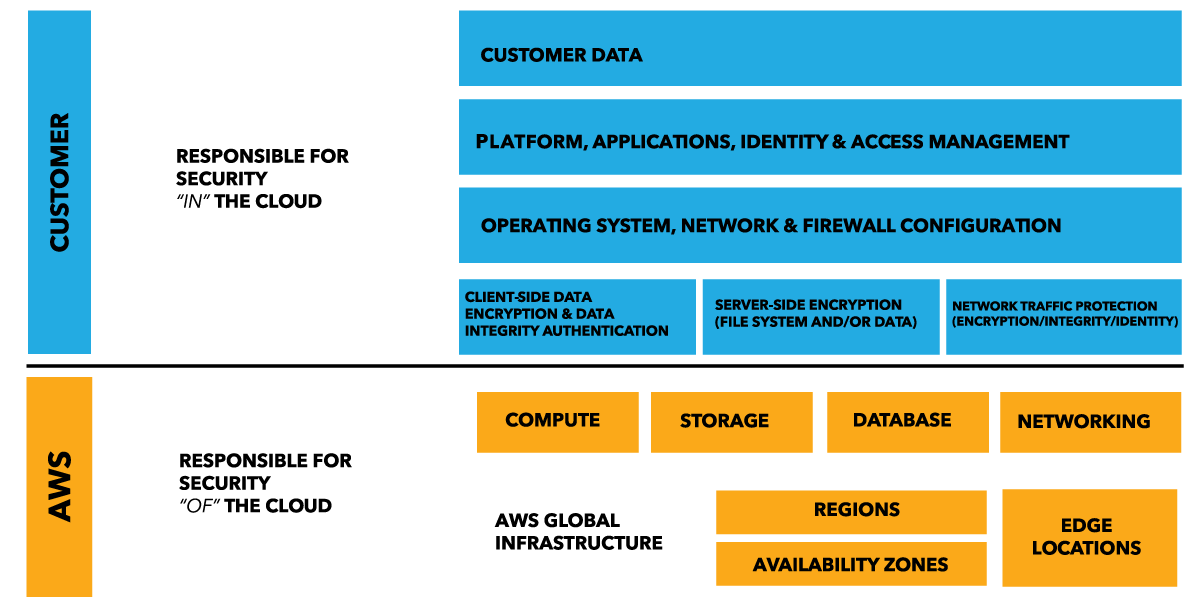
Cybersecurity
Cybersecurity Compliance: What, Why, and How in 2022?

Cybersecurity
9 Best Cybersecurity Podcasts to Follow [2023]
![9 Best Cybersecurity Podcasts to Follow [2023] 85 Cybersecurity Podcasts](https://www.eescorporation.com/wp-content/uploads/2021/10/CyberSecurity-Podcasts.jpeg)
Internet Technology
Best Cloud Security Tools in 2022

Cybersecurity
US Cybersecurity Statistics You Should Know In 2022

Cybersecurity
EV Cyber Security: How Secure Are Electric Vehicles?

Cybersecurity
Cyber Security Checklist to Make Smart Home Network Safe

Cybersecurity
Security Issues In Cloud Computing and Its Solution

IT Staffing
Guide To Hiring A Digital Marketing Talent
Digital Marketing
Cloud Computing for Marketing: How the cloud helps marketers in 2022?

Digital Marketing
Facebook Vs LinkedIn: Which is best for B2B marketing?

Datacenter Networking
Datacenter Marketing: Best Plan, Strategy and 10 Ideas
Digital Marketing
Why You Should Start Building Your Brand Strategy? Things to Consider

Digital Marketing
Top 5 Benefits of Enterprise SEO Services

E-Commerce
How is Machine Learning used in E-Commerce?

Cloud Computing
Migrating e-commerce to cloud: Benefits, And Tips

Artificial Intelligence
How AI can Improve Cloud Computing?

Artificial Intelligence
How Artificial Intelligence will Transform Business?
Artificial Intelligence
How to Use AI and Machine Learning for Cyber Security?

Artificial Intelligence
Why is AI Consulting Becoming Important?

Artificial Intelligence
How Artificial Intelligence is Transforming the World?

Artificial Intelligence
What Are The Benefits of Artificial Intelligence?

Artificial Intelligence
How to Use Artificial Intelligence Against Cyber Attack?

Artificial Intelligence
What are the Challenges of Artificial Intelligence?

Artificial Intelligence
How Artificial Intelligence Works with Web Design?

Artificial Intelligence
Artificial Intelligence in Business

Artificial Intelligence
What Are Explainable AI Principles?

Artificial Intelligence
Benefits of narrow artificial intelligence

Artificial Intelligence
25+ Artificial Intelligence Statistics and Facts In 2022

Artificial Intelligence
The Pros and Cons of Artificial Intelligence In Mobile Apps

Information Technology
Understanding How AI Can Enhance Datacenter Security: 8 Powerful Attributes

Business Intelligence
How would the Technology Industry use Business Intelligence?

Business Intelligence
What is the Future of Business Intelligence?

Decision Intelligence
Top Business Strategic Priorities To Be Followed By Business Leaders

Business Intelligence
Tips to Hire Business Intelligence (BI) Professionals
Business Intelligence
Business Intelligence Tools & Business Analytics: Important Facts You Must Know

Business Intelligence
Decision intelligence vs. business intelligence: How do both differ and relate?
Cloud Computing
Mainframe vs. Server: How Are They Different?

Datacenter Security
Tips for Hiring the Best Data Center Talent/Technicians

Datacenter Networking
What is Network Infrastructure Security?

Datacenter Networking
Network Servers Installation and Configuration: Essential Tips

Datacenter Networking
Network congestion: Introduction, causes, and solution

Datacenter Networking
Datacenter Tiers Classification Level (Tier 1,2,3,4)

Datacenter Networking
10+ Datacenters Statistics: Mind Blowing Facts and Figures

Datacenter Networking
How are Data Centers Connected to the Internet?

Datacenter Networking
Data Center Networking with Multipath TCP
Datacenter Networking
Datacenter Marketing: Best Plan, Strategy and 10 Ideas

Datacenter Networking
Pros and Cons: Containerized Data Center

Datacenter Networking
Colocation Data Center Guide – Overview, Merits And Demerits

Internet Technology
What Is The Difference Between A Data Center And Cloud Computing?

Datacenter Networking
Important Datacenter Network Topology Types Leading Business in 2022

Datacenter Networking
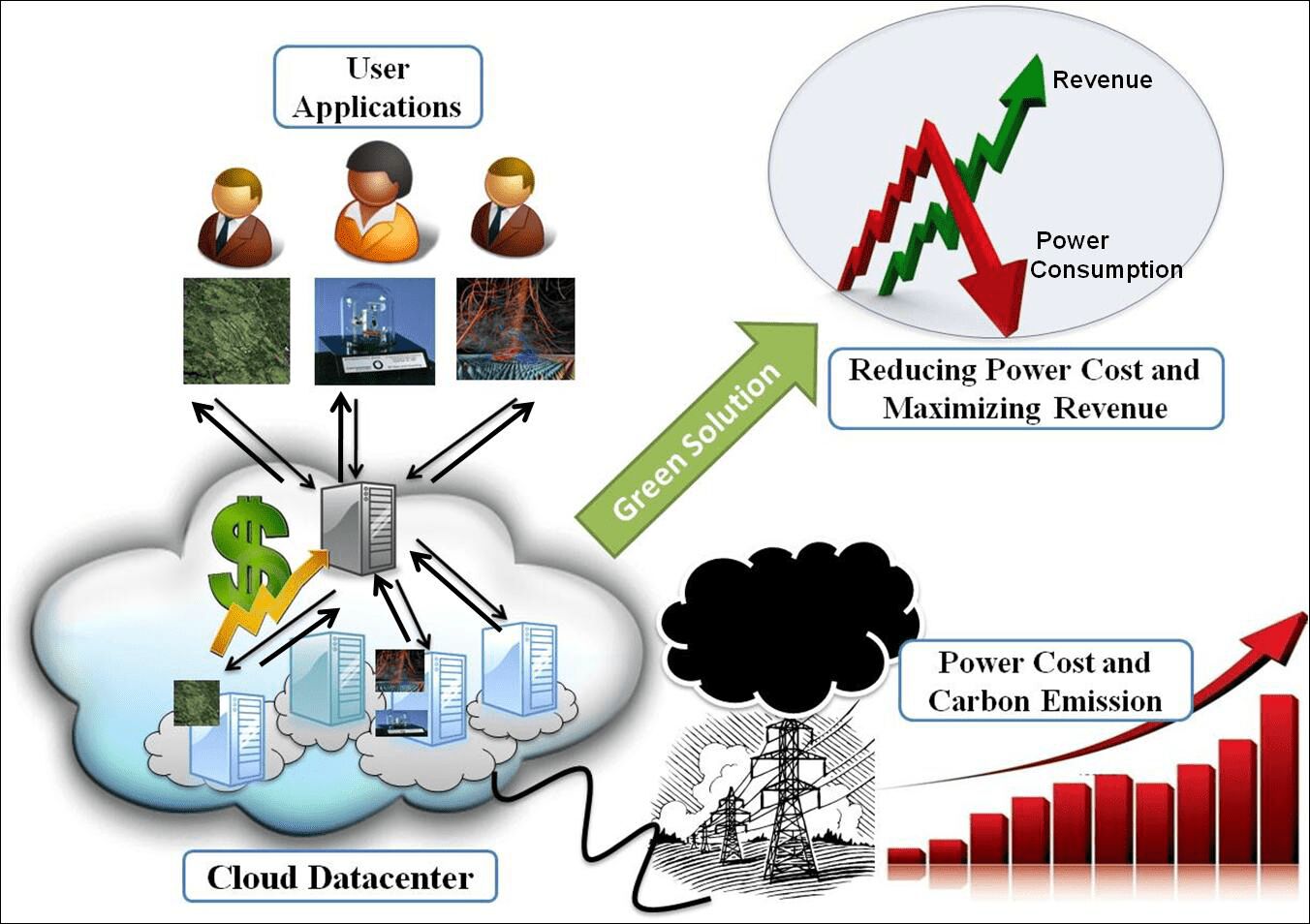
Energy Efficiency in Data Center Networking: 8 Helpful Solutions
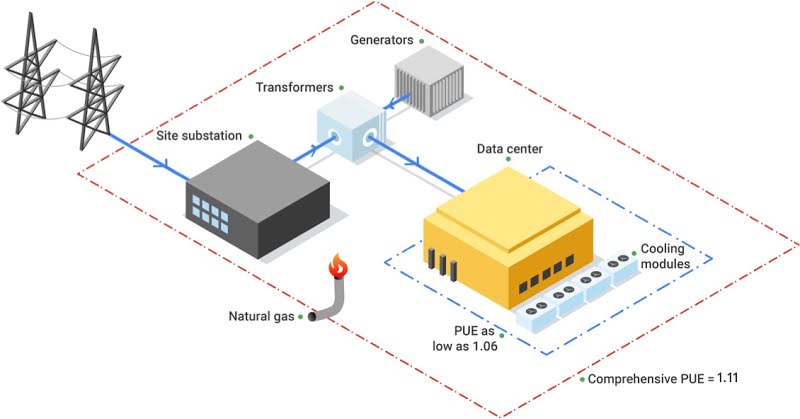
Datacenter Networking
Visual Data Modeling in Datacenter Networking: Important Features You Must Know In 2022
Datacenter Networking
7 Important Datacenter Networking Challenges You Would Loved to Know in 2022

Datacenter Networking
3 Data Center Networking Tips You Should Know

Datacenter Security
Tips for Hiring the Best Data Center Talent/Technicians

Datacenter Security
What Are The Data Center Security Levels?

Cybersecurity
Types of Security Controls

Datacenter Networking
10+ Datacenters Statistics: Mind Blowing Facts and Figures

Information Technology
The Top 4 Data Center Security Best Practices

Information Technology
Understanding How AI Can Enhance Datacenter Security: 8 Powerful Attributes

Datacenter Security
All You Need to Know About The Top 5 Datacenter Security Solutions

Datacenter Security
5 Ways to Improve Datacenter Security

Information Technology
Datacenter Vulnerabilities: 7 Life-Changing Attacks You Must Know

Datacenter Security
Important Network Infrastructure Security Trends For 2022

Datacenter Security
10 Best Data Center Security Tips You Should Know

Decision Intelligence
Top Business Strategic Priorities To Be Followed By Business Leaders

Information Technology
6 IT Management Traps To Avoid At All Costs

Information Technology
Guide On How to Hire Robotics Engineer
Machine Learning
How to Recruit Machine Learning Talent

Information Technology
How To Choose The Right Staffing Firm?

IT Staffing
Guide to Evaluate IT Candidates Remotely

IT Staffing
Guide To Hiring A Digital Marketing Talent

Information Technology
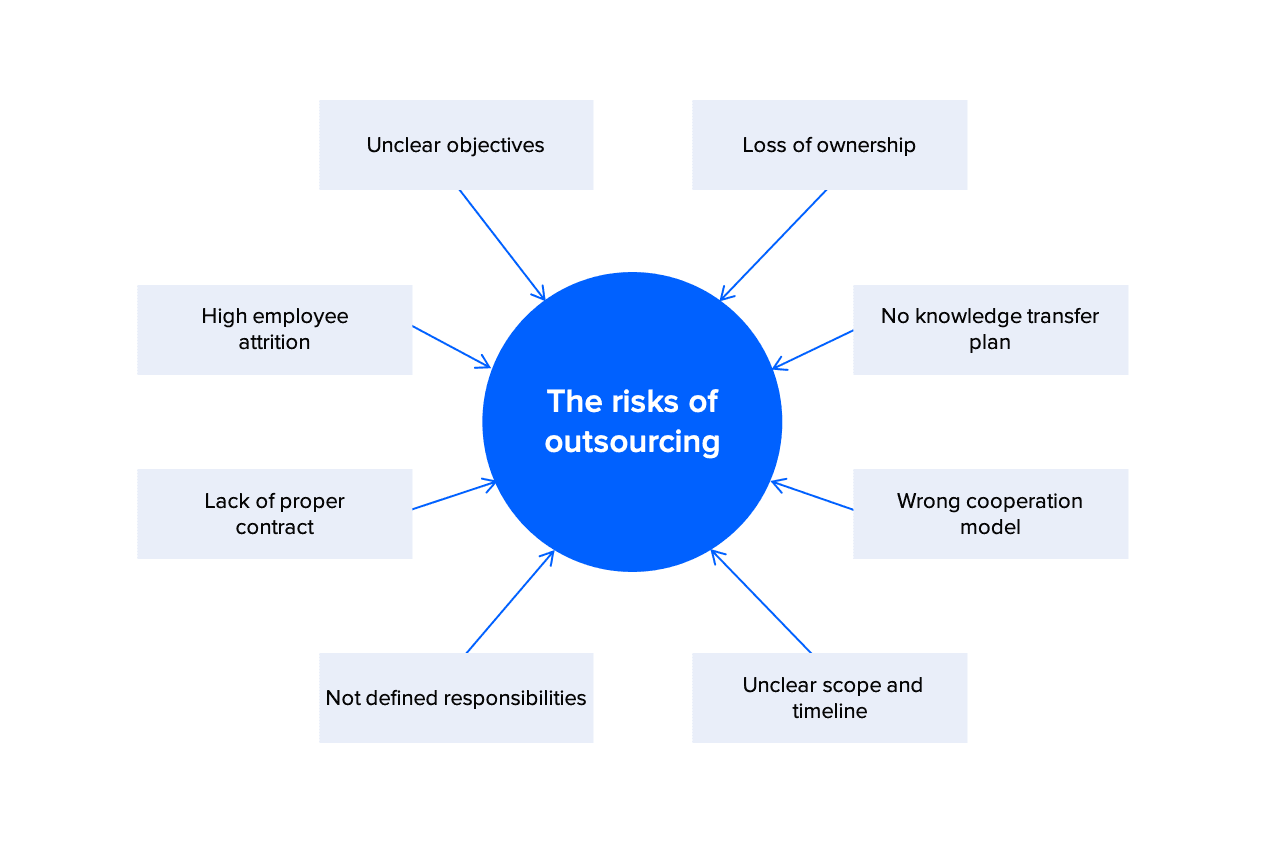
What are the Major Risks of outsourcing IT Services in 2022?
IT Staffing
Most Common Challenges In IT Recruitment

IT Staffing
How Can Cloud Computing Benefit IT Staff?
IT Staffing
Temporary vs Permanent IT Staffing: Pros & Cons

Information Technology
Why You should Invest in IT Training and Skill Development of Your Team?

E-Commerce
How is Machine Learning used in E-Commerce?

Machine Learning
What are the Business Benefits of Machine Learning?
Artificial Intelligence
How to Use AI and Machine Learning for Cyber Security?

Machine Learning
How is Machine Learning going to Impact all other Industries?

Machine Learning
How to Recruit Machine Learning Talent

Machine Learning
The Role of Machine Learning In Recruitment Process

Machine Learning
Best Data Cleaning Techniques In Machine Learning In 2022

Information Technology
30+ Amazing Machine Learning Statistics and Facts in 2022
Virtual/Augmented Reality
How is VR Used in Marketing?

Virtual/Augmented Reality
How is Virtual Reality different from Augmented Reality?
Virtual/Augmented Reality
How Does Augmented Reality Work?
Virtual/Augmented Reality
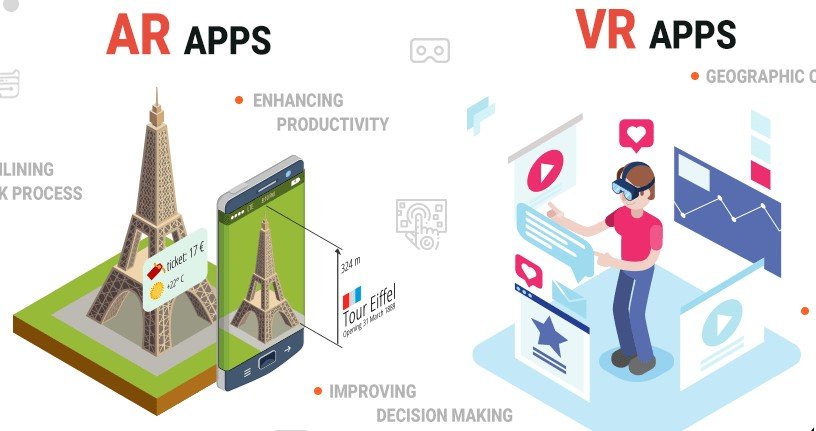
Augmented Reality vs Virtual Reality vs Mixed Reality

Virtual/Augmented Reality
5 Top Tools For VR And AR Development
Virtual/Augmented Reality
Ar and VR in Education: Extended Reality Uses
Cloud Computing
Accounting for Cloud Computing Arrangements

Financial Technology
10+ Fintech Statistics & Facts for 2022

Financial Technology
Do Robo Advisors Use Artificial Intelligence(AI) ?
Autonomous Systems
Reliability and Safety Aspects of Autonomous Systems

Electric Vehicle technology
EV Market Statistics and Forecasts for 2022 and Beyond
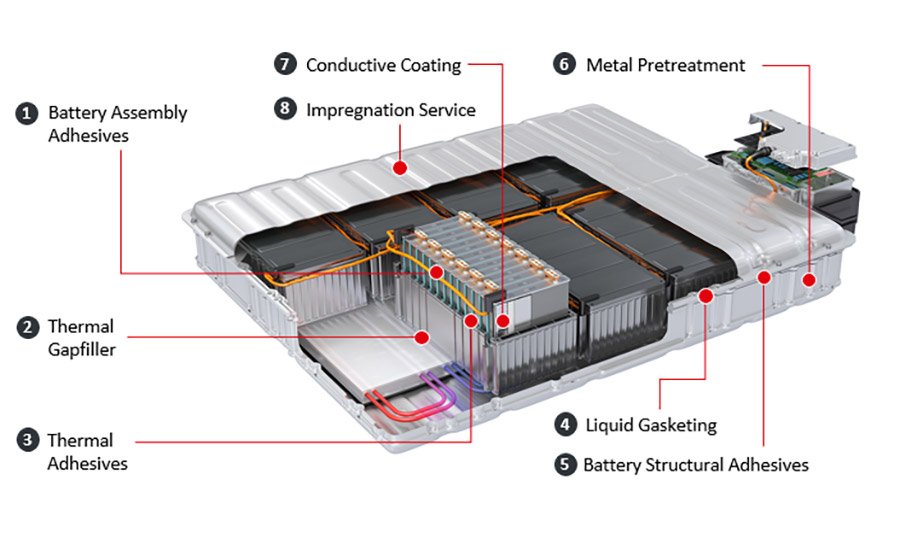
Electric Vehicle technology
Electric Vehicle Battery Technology Types And Their Cost
Electric Vehicle technology
How well do electric cars hold their value?

Cybersecurity
EV Cyber Security: How Secure Are Electric Vehicles?

Internet of Things
How Does IoT Impact Our Lives In Smart Homes And Cities?
Engineering Technology
5 Astonishing Key IOT Statistics to know in 2022

Internet of Things
Advantages of Internet of Things: 6 Benefits You Should Know

Internet of Things
How does IoT work? The 4 key components You Should Know.
Internet of Things
Internet of Things Examples: 12 Practical Ways To Better Your Understanding
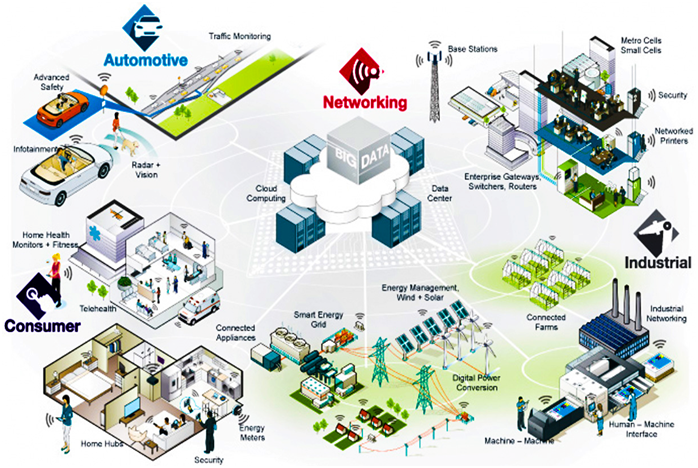
Internet of Things
Top 20 Internet of Things Facts You Should Know

Internet of Things
Top 10 Applications of Internet of Things. Practical Benefits

Quantum Computing
Quantum Computing in Cloud Computing: Their Relation and Future Scope

Renewable Energy
12 Ways Businesses Can Save Energy
Information Technology
Guide On How to Hire Robotics Engineer

Cloud Computing
Cloud computing in Robotics: How is Cloud Empowering Robotics?

Self-Driving Technology
Do Self-Driving Cars use Artificial Intelligence(AI)?

Internet of Things
How Does IoT Impact Our Lives In Smart Homes And Cities?

Smart homes
A Smart Home Checklist for Must-Have Devices
Cybersecurity
Cyber Security Checklist to Make Smart Home Network Safe

Software Engineering
Capgemini vs Infosys: Cloud and IT Services and Consulting Comparison

Software Engineering
10 Must-Know Features of a Great Mobile Application

Software Engineering
10 Best Project Management Tools For Software Development in 2022

Software Engineering
Feather Magazine Theme Vs Image Gridly Theme- A Comprehensive Comparison
Cloud Computing
10 Cloud Computing Applications in 2022

Systems engineering
How System Engineering Help In Risk Management