With the day-by-day advancements of technology, more and more impactful and valuable methods are being introduced to ease operational labor. “Cloud” or “Cloud Computing” is one of the advancements made in the modern era. A cloud is basically “all the stuff on the internet.” The data uploaded on the internet servers each second is being stored on millions of computers and storage devices all at once which are connected through various modes. That interconnected data has essentially termed the cloud, and this process of accessing the data and working with it is called cloud computing.
More and more organizations, whether small-scale organizations or multi-tenant groups with hundreds of employees are shifting to the cloud rapidly and getting “cloud-ready.”
What is Cloud Readiness Assessment?
It is the method in which an organization surveys its data and applications to determine whether they can be shifted to the cloud environment with minimal labor and effort. Cloud Readiness Assessment not only helps an organization to conclusively find out about the capabilities of their systems but also helps them to take adequate steps to shift to the cloud. Integrating the resources with the cloud can often be a very messy job and should be done with care. And this process helps you make sure a coherent integration with the cloud happens, and the mitigation with its resources is seamless.
With EES cloud computing consulting services, you can harness the real benefits of the advanced, secure, reliable, and scalable cloud environment. We assist from cloud migration to cloud optimization at surprisingly lower operational costs because quality is what we focus on!
In this article, we will discuss the guidelines for an effective Cloud Readiness Assessment and the steps taken to ensure it. But the most important part is not how it is, however, the why and what. Before shifting all your resources to the cloud, it is imperative to make sure why you need a shift in the first place? If you don’t know why you should migrate to the cloud, it is the same as driving without headlights.
Reasons and Goals for Integrating into The Cloud
- To maintain economic balance
- Increased productivity and scalability
- Increased collaboration with the resources
- Improving the fail-over capacity of the system.
One thing which should also be highlighted here is the organization. Before moving to the cloud, the organization should know what resources to integrate with the cloud and what resources should be left untouched, as moving all your eggs in a single basket could prove fatal in the long run.
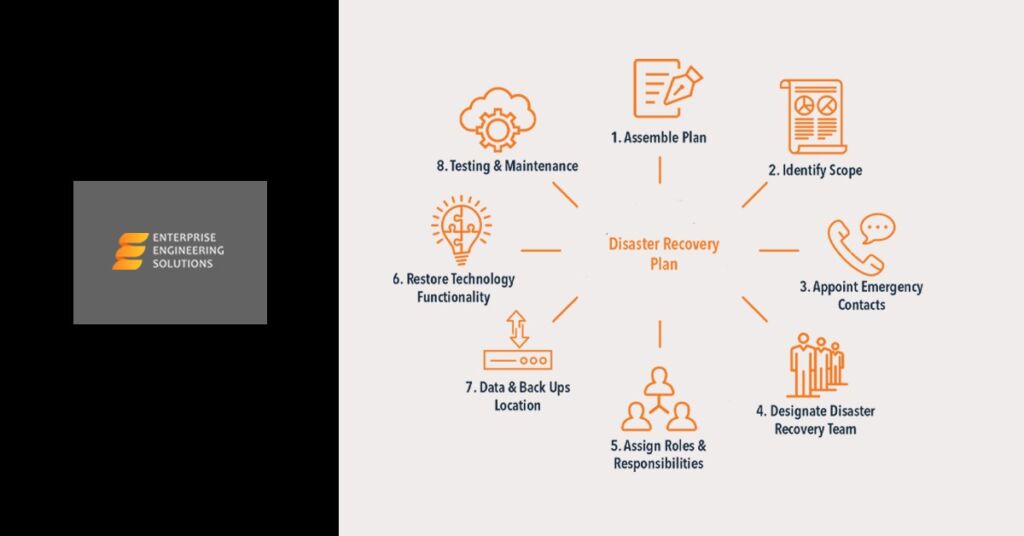
Cloud Readiness Assessment Guide
Following are some important steps in guiding one towards a seamless shift to the evergreen and upcoming cloud environment:
Finding Out the Scope and Business Objectives Towards the Shift
An organization should have a crystal clear image of why it should move to the cloud and to what extent. Once the reasons for the move are decided, an organization should be clear about what of its resources should be moved to the cloud as it would be foolish and problematic to shift all of its data and resources to the cloud. One example could be the security and authentication resources which ensure the company about the privacy and administrative settings of an organization. They should be in the authoritative control of the organization itself.
Some business objectives for shifting towards the cloud are as follows:
- To maintain economic balance
- Increased productivity and scalability
- Increased collaboration with the resources
- Improving the fail-over capacity of the system.
Analyze The Potential of Your Resources and Fill the Gaps
The next major goal is to analyze and scrutinize the resources at your disposal—the IT team, for example. You should know what potential they have and do they even have enough knowledge for shifting to a cloud-based environment or not. Once you analyze, you need to fill in the gaps where necessary. Following are the things you should look for in your resources:
- Do they possess the right and real skills for such a task
- Are they fully available on the scene for the mitigation
- Do they have any prior experience
- Do they have the right tools and technologies
If you identify any shortcomings among the points mentioned above, you should immediately adhere to damage control and fix the problems. One way to make your IT staff more productive in itself is to educate them on new and upcoming technologies and organize workshops and seminars for them to be further guided about cloud readiness assessment.
Assess Infrastructure Requirements
An organization must do internal research within its resources and its infrastructure to ensure that they have all the possible resources, applications, and tools required for a move towards the cloud. Planning for a new environment or shifting on a large scale can take a load on the company’s resources, tools, and applications, and they should have future planning beforehand. The steps taken now will ensure the feasibility of your organization; otherwise, all the resources could choke.
The following can be important requirements regarding infrastructure that need to be assessed:
- Modification of the applications
- Costs and technologies used
- Application dependencies
Security Needs
Whenever an organization makes a shift from conventional ways of computing towards a more advanced method such as cloud environment, security and privacy is one of the main concerns of a company. Choosing the right cloud platform is the primitive need of a company. When choosing to migrate to a cloud-based environment, it is essential that they keep in mind all the key factors behind such an environment. You need to assess the provider’s cloud-based system and select the one best meeting your security requirements.
Following are some of the security concerns highlighted in the Cloud Readiness Assessment:
- Firewall security
- Access management
- Identity management
Budgeting
Many companies decide to mitigate towards a cloud-based environment before discussing the costing and budgeting of the whole process. A company needs to manage its budgeting policies beforehand as it is one of the biggest challenges in choosing a cloud-based environment. The best practice is to decide on a budget and stick to it. Without proper reasoning and planning, such an infrastructure can surpass the estimated cost value, and organizations can be led to a mismanagement of a situation.
Some key parameters to be considered are:
- Usage (per month/year)
- Growth rate
- Maintenance, Automation, etc.
- Average resources
Final Verdict
All in all, it can be said that cloud-based environments are the talk of the town these days, but choosing and shifting to it is a rather intricate process and requires adequate thinking and planning. With good reasoning and planning or Cloud Readiness Assessment, one can choose a good cloud-based for its needs and have a profound and profitable future.